AWS
Please check the general requirements for basic requirements. On this page, we include AWS-specific recommendations.
Setting up Domain Name
For a seamless integration experience, we recommend using AWS Route 53.
Configuring Network
Check the network and firewall requirements section from the general requirements.
Please follow AWS VPC creation guide to set up your VPC, subnets, security groups, etc.
Your subnets will need to have correct tags below in order to provision the load balancer for nginx ingress
- common tag for both public subnets and private subnets:
kubernetes.io/cluster/${cluster-name}:ownedorshared - public subnets be tagged with:
kubernetes.io/role/elb(for an internet-facing load balancer) - private subnets be tagged with:
kubernetes.io/role/internal-elb(for an internal/private load balancer)
To create AWS ElastiCache Redis clusters, both the AWS VPC and subnets must have the tag:
redis/discovery: ${cluster-name}.
Please contact AlphaSense if you need extra annotations to the nginx ingress service kind specified in cloud-provider-aws
Kubernetes Cluster
CNI
We recommend using EKS default CNI or Cilium.
Amazon EBS Storage
Make sure the AWS EBS CSI driver is installed and working.
Node Groups Configuration
Select one of the reference architectures and configure the node group auto-scaling accordingly.
We haven't fully migrated all applications to IMDSv2.
All nodegroup will need below InstanceMetadataOptionsRequest:
HttpEndpoint: enabled
HttpPutResponseHopLimit: 2
HttpTokens: required
Above are also default configurations for EKS managed nodegroup. Ref:
We included NVIDIA GPU Operator to configure the driver for Ubuntu AMI kernel.
If you use eksctl to create the cluster, please add the flag --install-nvidia-plugin=false
eksctl create cluster -f cluster.yaml --install-nvidia-plugin=false
Example of eksctl configuration that would set up the VPC, cluster, EBS CSI driver, OIDC, and needed role for Karpenter.
Please adapt the configuration to meet your security compliance.
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: ${CLUSTER_NAME}
region: ${LOCATION}
version: '1.29'
tags:
karpenter.sh/discovery: ${CLUSTER_NAME}
iam:
withOIDC: true
vpcResourceControllerPolicy: true
karpenter:
version: '1.0.7' # Exact version must be provided
createServiceAccount: true
withSpotInterruptionQueue: false
vpc:
cidr: '172.16.0.0/16'
autoAllocateIPv6: false
clusterEndpoints:
publicAccess: true
nat:
gateway: HighlyAvailable
addons:
- name: vpc-cni
version: latest
- name: coredns
version: latest
- name: kube-proxy
version: latest
- name: aws-ebs-csi-driver
version: latest
managedNodeGroups: # this has needed imds v2 configurations by default
- name: bootstrap
instanceType: m6a.2xlarge
desiredCapacity: 2
minSize: 2
volumeEncrypted: true
volumeSize: 100
updateConfig:
maxUnavailable: 1
labels:
type: default
ssh:
allow: true
publicKeyName: <your public key name>
privateNetworking: true
iam:
withAddonPolicies:
externalDNS: true
certManager: true
ebs: true
fsx: false
efs: false
Example of a Karpenter nodepool and ec2nodeclass
Please add all needed nodepool and ec2nodeclass with the right labels and taints as specified above.
apiVersion: karpenter.sh/v1
kind: NodePool
metadata:
name: gpu-t4-xlarge
spec:
template:
metadata:
labels:
type: gpu
'gpu.type': T4
spec:
requirements:
- key: karpenter.sh/capacity-type
operator: In
values: ['on-demand']
- key: node.kubernetes.io/instance-type
operator: In
values: ['g4dn.xlarge']
nodeClassRef:
group: karpenter.k8s.aws
kind: EC2NodeClass
name: gpu-t4-xlarge
expireAfter: 720h # 30d * 24h = 720h
limits:
cpu: 1000
nvidia.com/gpu: 6
disruption:
consolidationPolicy: WhenEmptyOrUnderutilized
consolidateAfter: 15m
---
apiVersion: karpenter.k8s.aws/v1
kind: EC2NodeClass
metadata:
name: gpu-t4-xlarge
spec:
metadataOptions: # required imds v2 configurations
httpEndpoint: enabled
httpPutResponseHopLimit: 2
httpTokens: required
amiFamily: AL2 # for userData template, ref: https://karpenter.sh/v1.0/concepts/nodeclasses/#specamifamily
instanceProfile: 'eksctl-KarpenterNodeInstanceProfile-${CLUSTER_NAME}'
blockDeviceMappings:
- deviceName: /dev/sda1
ebs:
volumeSize: 100Gi
volumeType: gp3
encrypted: true
rootVolume: true
subnetSelectorTerms:
- tags:
karpenter.sh/discovery: '${CLUSTER_NAME}'
kubernetes.io/role/internal-elb: '1' # private subnets
securityGroupSelectorTerms:
- tags:
karpenter.sh/discovery: '${CLUSTER_NAME}'
Name: eksctl-${CLUSTER_NAME}-cluster/ClusterSharedNodeSecurityGroup
amiSelectorTerms:
- name: ubuntu-eks/k8s_1.30/images/hvm-ssd/ubuntu-jammy-22.04-amd64-server-20240729
owner: '099720109477' # Canonical account id
tags:
Name: gpu-t4-xlarge-${CLUSTER_NAME}
S3 Buckets
AlphaSense uses Crossplane to create around 30 buckets. The AWS account where you plan to install must have enough free space to create those buckets.
MySQL Database Cluster
Please check the engine and required parameters in the
MySQL database cluster section of the general
requirements.
We recommend using Aurora MySQL.
If you use Aurora MySQL, please follow the parameter groups docs to configure the server parameters.
Example AWS CLI command to create the cluster parameter group
aws rds create-db-cluster-parameter-group --db-cluster-parameter-group-name "${CLUSTER_NAME}-cluster-parameter-group" --db-parameter-group-family aurora-mysql5.7 --description shared
aws rds modify-db-cluster-parameter-group --db-cluster-parameter-group-name "${CLUSTER_NAME}-cluster-parameter-group" --parameters \
ParameterName=wait_timeout,ParameterValue=1800,ApplyMethod=immediate \
ParameterName=connect_timeout,ParameterValue=20,ApplyMethod=immediate \
ParameterName=net_read_timeout,ParameterValue=60,ApplyMethod=immediate \
ParameterName=net_write_timeout,ParameterValue=120,ApplyMethod=immediate \
ParameterName=innodb_print_all_deadlocks,ParameterValue=1,ApplyMethod=immediate \
ParameterName=lower_case_table_names,ParameterValue=1,ApplyMethod=pending-reboot
PostgreSQL Database Cluster
Please check the engine and required parameters in the
PostgreSQL database cluster section of the
general requirements.
We recommend using Aurora PostgreSQL.
IAM Roles for Service Accounts (IRSA)
We support only IRSA; no support for EKS Pod Identity.
Customers will need to set up an OIDC provider and the required IAM roles and policies for Crossplane controller pods. AlphaSense provides Crossplane controllers in the installation manifests which will assume the customer-provided role to create pods' IRSA, SNS, SQS, S3, and DynamoDB as detailed below.
AWS IAM Role & Policy Setup
export AWS_PROFILE=<aws profile where you want to install the AlphaSense EI product>
export CLUSTER_NAME=<your cluster name, e.g. thunderstorm>
export ACCOUNT_ID=<aws account id, i.e: 683356991689>
export OIDC_ID=<OIDC id, i.e: oidc.eks.us-east-1.amazonaws.com/id/7B05FD51D86B2B7249D2A21521E477EE>
Establish one essential role for Crossplane to provision AWS cloud resources.
OIDC Provider for IAM Role for Service Account
Please follow the guide to create an OIDC provider and associate it with the Kubernetes cluster.
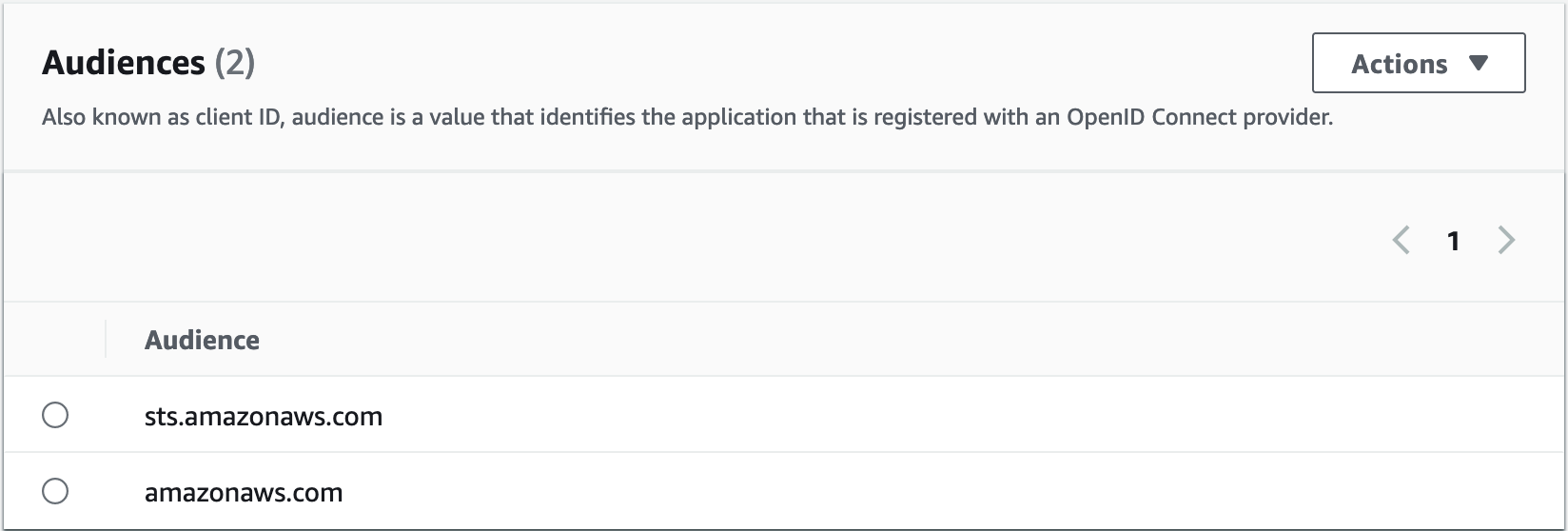
Make sure the OIDC provider has these audiences:
- amazonaws.com
- sts.amazonaws.com
Note down the OIDC ID. For example:
oidc.eks.us-east-1.amazonaws.com/id/7B05FD51D86B2B7249D2A21521E477EE.
Please input the exact OIDC ID during the installation.
The OIDC ID must look like oidc.eks.us-east-1.amazonaws.com/id/7B05FD51D86B2B7249D2A21521E477EE,
for example.
Please do not include the https:// prefix.
Crossplane Managed Identity
To enable Crossplane to create all the necessary resources and permissions, a role must be created. The following examples and lists are provided for audit purposes. You can decide how to create the role and identity, whether through Terraform or another method of your choice.
Remember to replace placeholders in commands with your actual information during execution.
cat << 'EOF' > crossplane_role_trust.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::${ACCOUNT_ID}:oidc-provider/${OIDC_ID}"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringLike": {
"${OIDC_ID}:sub": "system:serviceaccount:crossplane:aws-*"
}
}
}
]
}
EOF
The crossplane_role_trust.json file defines the trust relationship policy for the Crossplane IAM
role. This policy specifies which entities are allowed to assume the role and under what conditions.
In this case, the policy allows the role to be assumed by a federated identity from the specified OIDC provider.
The Condition section further restricts the assumption of the role to service accounts within the
crossplane namespace that match the pattern aws-*.
cat << 'EOF' > crossplane_boundary.json
{
"Statement": [
{
"Effect": "Allow",
"NotAction": [
"support:*",
"organizations:*",
"iam:Upload*",
"iam:Update*",
"iam:Untag*",
"iam:Tag*",
"iam:Set*",
"iam:Resync*",
"iam:Reset*",
"iam:Remove*",
"iam:Put*",
"iam:PassRole",
"iam:ListVirtualMFA*",
"iam:ListMFA*",
"iam:GetOrganizationsAccessReport",
"iam:GetAccountAuthorizationDetails",
"iam:Generate*",
"iam:Enable*",
"iam:Detach*",
"iam:Delete*",
"iam:Deactivate*",
"iam:Create*",
"iam:Change*",
"iam:Attach*",
"iam:Add*",
"cloudtrail:DeleteTrail"
],
"Resource": "*",
"Sid": "AllowAllActionsApartFromListed"
}
],
"Version": "2012-10-17"
}
EOF
The crossplane_boundary.json file defines a permissions boundary for the IAM roles for service
accounts
(IRSA)
created by Crossplane. Each application pod will have an IRSA with fine-grain access control,
allowing the application to access only the resources it needs. This boundary prevents the
application from using high privilege IAM permissions by denying the actions explicitly listed in
the NotAction section.
The table below explains the permissions granted in crossplane_boundary.json
| Permission | Description |
|---|---|
support:* | Denied. Prevents any support-related actions. |
organizations:* | Denied. Prevents any actions related to AWS Organizations. |
iam:Upload* | Denied. Prevents uploading any IAM resources. |
iam:Update* | Denied. Prevents updating any IAM resources. |
iam:Untag* | Denied. Prevents removing tags from IAM resources. |
iam:Tag* | Denied. Prevents adding tags to IAM resources. |
iam:Set* | Denied. Prevents setting any IAM configurations. |
iam:Resync* | Denied. Prevents resynchronizing IAM resources. |
iam:Reset* | Denied. Prevents resetting any IAM configurations. |
iam:Remove* | Denied. Prevents removing any IAM resources. |
iam:Put* | Denied. Prevents putting any IAM configurations. |
iam:PassRole | Denied. Prevents passing any IAM roles. |
iam:ListVirtualMFA* | Denied. Prevents listing virtual MFA devices. |
iam:ListMFA* | Denied. Prevents listing MFA devices. |
iam:GetOrganizationsAccessReport | Denied. Prevents getting access reports for organizations. |
iam:GetAccountAuthorizationDetails | Denied. Prevents getting account authorization details. |
iam:Generate* | Denied. Prevents generating any IAM resources. |
iam:Enable* | Denied. Prevents enabling any IAM configurations. |
iam:Detach* | Denied. Prevents detaching any IAM policies. |
iam:Delete* | Denied. Prevents deleting any IAM resources. |
iam:Deactivate* | Denied. Prevents deactivating any IAM configurations. |
iam:Create* | Denied. Prevents creating any IAM resources. |
iam:Change* | Denied. Prevents changing any IAM configurations. |
iam:Attach* | Denied. Prevents attaching any IAM policies. |
iam:Add* | Denied. Prevents adding any IAM resources. |
cloudtrail:DeleteTrail | Denied. Prevents deleting CloudTrail trails. |
cat << 'EOF' > crossplane.json
{
"Statement": [
{
"Action": [
"iam:Update*",
"iam:Put*",
"iam:DetachRolePolicy",
"iam:DeleteRolePolicy",
"iam:AttachRolePolicy"
],
"Effect": "Deny",
"Resource": "arn:aws:iam::${ACCOUNT_ID}:role/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}",
"Sid": "DenyAlteringOwnRole"
},
{
"Action": [
"iam:SetDefaultPolicyVersion",
"iam:DeletePolicyVersion",
"iam:DeletePolicy",
"iam:CreatePolicyVersion"
],
"Effect": "Deny",
"Resource": "arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}-boundary",
"Sid": "DenyAlteringPermissionsBoundary"
},
{
"Action": "iam:DeleteRolePermissionsBoundary",
"Effect": "Deny",
"Resource": "*",
"Sid": "DenyDeletingAnyPermissionsBoundary"
},
{
"Action": "sts:GetCallerIdentity",
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowCallSTSToGetCurrentIdentity"
},
{
"Action": [
"iam:PutRolePolicy",
"iam:PutRolePermissionsBoundary",
"iam:DetachRolePolicy",
"iam:DeleteRolePolicy",
"iam:CreateRole",
"iam:AttachRolePolicy"
],
"Condition": {
"StringEquals": {
"iam:PermissionsBoundary": "arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}-boundary"
}
},
"Effect": "Allow",
"Resource": "arn:aws:iam::${ACCOUNT_ID}:role/web-identity/${CLUSTER_NAME}/crossplane/*",
"Sid": "EnforcePermissionBoundaryOnSpecificIAMActions"
},
{
"Action": [
"iam:List*",
"iam:GetRole*",
"iam:GetPolicy*"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowReadnListAllIAMRolesAndPolicies"
},
{
"Action": [
"iam:UpdateRoleDescription",
"iam:UpdateRole",
"iam:UpdateAssumeRolePolicy",
"iam:UntagRole",
"iam:TagRole",
"iam:ListAttachedRolePolicies",
"iam:DeleteRole"
],
"Effect": "Allow",
"Resource": "arn:aws:iam::${ACCOUNT_ID}:role/web-identity/${CLUSTER_NAME}/crossplane/*",
"Sid": "AllowCertainIAMActionsWithManagedRoles"
},
{
"Action": [
"iam:UntagPolicy",
"iam:TagPolicy",
"iam:DeletePolicy*",
"iam:CreatePolicy*"
],
"Effect": "Allow",
"Resource": "arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane/*",
"Sid": "AllowCertainIAMActionsWithManagedPolicies"
},
{
"Action": [
"s3:ReplicateDelete",
"s3:PutStorageLensConfiguration",
"s3:PutReplicationConfiguration",
"s3:PutLifecycleConfiguration",
"s3:PutIntelligentTieringConfiguration",
"s3:PutEncryptionConfiguration",
"s3:PutBucket*",
"s3:PutAccelerateConfiguration",
"s3:List*",
"s3:Get*",
"s3:DeleteStorageLensConfiguration",
"s3:CreateBucket"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowS3BucketCreation"
},
{
"Action": [
"dynamodb:UpdateTimeToLive",
"dynamodb:UpdateTable",
"dynamodb:UpdateGlobalTableSettings",
"dynamodb:UpdateGlobalTable",
"dynamodb:UpdateContinuousBackups",
"dynamodb:UntagResource",
"dynamodb:TagResource",
"dynamodb:ListTagsOfResource",
"dynamodb:ListTables",
"dynamodb:ListStreams",
"dynamodb:ListImports",
"dynamodb:ListGlobalTables",
"dynamodb:ListExports",
"dynamodb:ListContributorInsights",
"dynamodb:ListBackups",
"dynamodb:DescribeTimeToLive",
"dynamodb:DescribeTable",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DeleteTable",
"dynamodb:CreateTable",
"dynamodb:CreateGlobalTable"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowDynamoDB"
},
{
"Action": [
"sns:UntagResource",
"sns:Unsubscribe",
"sns:TagResource",
"sns:Subscribe",
"sns:SetTopicAttributes",
"sns:SetSubscriptionAttributes",
"sns:SetEndpointAttributes",
"sns:ListTopics",
"sns:ListTagsForResource",
"sns:ListSubscriptionsByTopic",
"sns:ListSubscriptions",
"sns:ListSMSSandboxPhoneNumbers",
"sns:ListPlatformApplications",
"sns:ListOriginationNumbers",
"sns:ListEndpointsByPlatformApplication",
"sns:GetTopicAttributes",
"sns:GetSubscriptionAttributes",
"sns:GetEndpointAttributes",
"sns:DeleteTopic",
"sns:DeleteEndpoint",
"sns:CreateTopic",
"sns:ConfirmSubscription"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowSNS"
},
{
"Action": [
"sqs:UntagQueue",
"sqs:TagQueue",
"sqs:SetQueueAttributes",
"sqs:ReceiveMessage",
"sqs:ListQueues",
"sqs:ListQueueTags",
"sqs:ListDeadLetterSourceQueues",
"sqs:GetQueueUrl",
"sqs:GetQueueAttributes",
"sqs:DeleteQueue",
"sqs:CreateQueue"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowSQS"
}
],
"Version": "2012-10-17"
}
EOF
cat << 'EOF' > crossplane-redis.json
{
"Statement": [
{
"Action": [
"ec2:DescribeSecurityGroups",
"ec2:DescribeSecurityGroupRules",
"ec2:ModifySecurityGroupRules",
"ec2:CreateSecurityGroup",
"ec2:DeleteSecurityGroup",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:AuthorizeSecurityGroupEgress",
"ec2:RevokeSecurityGroupIngress",
"ec2:RevokeSecurityGroupEgress",
"ec2:CreateTags",
"ec2:DeleteTags",
"ec2:DescribeTags",
"ec2:DescribeVpcs",
"ec2:DescribeSubnets",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRouteTables",
"ec2:DescribeVpcEndpoints"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowEC2ForRedisInfrastructure"
},
{
"Action": [
"elasticache:CreateUser",
"elasticache:DescribeReservedCacheNodes",
"elasticache:DescribeReservedCacheNodesOfferings",
"elasticache:DescribeEvents",
"elasticache:IncreaseReplicaCount",
"elasticache:DescribeCacheParameterGroups",
"elasticache:DecreaseReplicaCount",
"elasticache:DescribeEngineDefaultParameters",
"elasticache:CreateGlobalReplicationGroup",
"elasticache:ModifyReplicationGroup",
"elasticache:CreateCacheCluster",
"elasticache:DeleteCacheSubnetGroup",
"elasticache:DescribeServiceUpdates",
"elasticache:DescribeReplicationGroups",
"elasticache:ModifyUserGroup",
"elasticache:DeleteUser",
"elasticache:RemoveTagsFromResource",
"elasticache:DeleteUserGroup",
"elasticache:DeleteCacheCluster",
"elasticache:AddTagsToResource",
"elasticache:ModifyCacheParameterGroup",
"elasticache:DescribeGlobalReplicationGroups",
"elasticache:DescribeUsers",
"elasticache:DescribeCacheClusters",
"elasticache:ListTagsForResource",
"elasticache:CreateReplicationGroup",
"elasticache:AuthorizeCacheSecurityGroupIngress",
"elasticache:DeleteCacheSecurityGroup",
"elasticache:DescribeCacheEngineVersions",
"elasticache:DescribeCacheSubnetGroups",
"elasticache:CreateCacheSubnetGroup",
"elasticache:DescribeSnapshots",
"elasticache:CreateCacheParameterGroup",
"elasticache:DeleteCacheParameterGroup",
"elasticache:DescribeUserGroups",
"elasticache:DisassociateGlobalReplicationGroup",
"elasticache:CreateCacheSecurityGroup",
"elasticache:DescribeCacheParameters",
"elasticache:CreateUserGroup",
"elasticache:DescribeUpdateActions",
"elasticache:ModifyUser",
"elasticache:DeleteGlobalReplicationGroup",
"elasticache:ResetCacheParameterGroup",
"elasticache:DeleteReplicationGroup",
"elasticache:ListAllowedNodeTypeModifications",
"elasticache:ModifyCacheCluster",
"elasticache:ModifyGlobalReplicationGroup",
"elasticache:DescribeCacheSecurityGroups",
"elasticache:ModifyReplicationGroupShardConfiguration",
"elasticache:ModifyCacheSubnetGroup"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowElasticache"
},
{
"Action": [
"iam:CreateServiceLinkedRole"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "AllowIAMForServiceLinkedRoles"
}
],
"Version": "2012-10-17"
}
EOF
The crossplane.json and crossplane-redis.json file defines a set of IAM policies that are
applied to the Crossplane provider role. These policies specify which actions are allowed or denied
for the role, ensuring that the role operates within the defined security boundaries.
The table below explains the permissions granted and denied in crossplane.json
DenyAlteringOwnRole
| Permission | Description |
|---|---|
iam:Update* | Denied. Prevents updating any IAM resources. |
iam:Put* | Denied. Prevents putting any IAM configurations. |
iam:DetachRolePolicy | Denied. Prevents detaching role policies. |
iam:DeleteRolePolicy | Denied. Prevents deleting role policies. |
iam:AttachRolePolicy | Denied. Prevents attaching role policies. |
The above actions are denied for the resource
arn:aws:iam::${ACCOUNT_ID}:role/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}
to prevent altering its own role.
DenyAlteringPermissionsBoundary
| Permission | Description |
|---|---|
iam:SetDefaultPolicyVersion | Denied. Prevents setting the default policy version. |
iam:DeletePolicyVersion | Denied. Prevents deleting policy versions. |
iam:DeletePolicy | Denied. Prevents deleting policies. |
iam:CreatePolicyVersion | Denied. Prevents creating policy versions. |
The above actions are denied for the resource
arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}-boundary
to prevent altering the permissions boundary.
DenyDeletingAnyPermissionsBoundary
| Permission | Description |
|---|---|
iam:DeleteRolePermissionsBoundary | Denied. Prevents deleting any permissions boundary. |
The above action is denied for all resources to prevent deleting any permissions boundary.
AllowCallSTSToGetCurrentIdentity
| Permission | Description |
|---|---|
sts:GetCallerIdentity | Allowed. Permits calling STS to get the current identity. |
The above action is allowed for all resources to enable getting the current identity.
EnforcePermissionBoundaryOnSpecificIAMActions
| Permission | Description |
|---|---|
iam:PutRolePolicy | Allowed. Permits putting role policies. |
iam:PutRolePermissionsBoundary | Allowed. Permits putting role permissions boundaries. |
iam:DetachRolePolicy | Allowed. Permits detaching role policies. |
iam:DeleteRolePolicy | Allowed. Permits deleting role policies. |
iam:CreateRole | Allowed. Permits creating roles. |
iam:AttachRolePolicy | Allowed. Permits attaching role policies. |
The above actions are allowed for the resource
arn:aws:iam::${ACCOUNT_ID}:role/web-identity/${CLUSTER_NAME}/crossplane/* with the condition that
the permissions boundary is
arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}-boundary.
AllowReadnListAllIAMRolesAndPolicies
| Permission | Description |
|---|---|
iam:List* | Allowed. Permits listing IAM resources. |
iam:GetRole* | Allowed. Permits getting role information. |
iam:GetPolicy* | Allowed. Permits getting policy information. |
The above actions are allowed for all resources to enable reading and listing all IAM roles and policies.
AllowCertainIAMActionsWithManagedRoles
| Permission | Description |
|---|---|
iam:UpdateRoleDescription | Allowed. Permits updating role descriptions. |
iam:UpdateRole | Allowed. Permits updating roles. |
iam:UpdateAssumeRolePolicy | Allowed. Permits updating assume role policies. |
iam:UntagRole | Allowed. Permits removing tags from roles. |
iam:TagRole | Allowed. Permits adding tags to roles. |
iam:ListAttachedRolePolicies | Allowed. Permits listing attached role policies. |
iam:DeleteRole | Allowed. Permits deleting roles. |
The above actions are allowed for the resource
arn:aws:iam::${ACCOUNT_ID}:role/web-identity/${CLUSTER_NAME}/crossplane/* to enable certain IAM
actions with managed roles.
AllowCertainIAMActionsWithManagedPolicies
| Permission | Description |
|---|---|
iam:UntagPolicy | Allowed. Permits removing tags from policies. |
iam:TagPolicy | Allowed. Permits adding tags to policies. |
iam:DeletePolicy* | Allowed. Permits deleting policies. |
iam:CreatePolicy* | Allowed. Permits creating policies. |
The above actions are allowed for the resource
arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane/* to enable certain IAM
actions with managed policies.
AllowS3BucketCreation
| Permission | Description |
|---|---|
s3:ReplicateDelete | Allowed. Permits replicating delete markers. |
s3:PutStorageLensConfiguration | Allowed. Permits putting storage lens configurations. |
s3:PutReplicationConfiguration | Allowed. Permits putting replication configurations. |
s3:PutLifecycleConfiguration | Allowed. Permits putting lifecycle configurations. |
s3:PutIntelligentTieringConfiguration | Allowed. Permits putting intelligent tiering configurations. |
s3:PutEncryptionConfiguration | Allowed. Permits putting encryption configurations. |
s3:PutBucket* | Allowed. Permits putting bucket configurations. |
s3:PutAccelerateConfiguration | Allowed. Permits putting accelerate configurations. |
s3:List* | Allowed. Permits listing S3 resources. |
s3:Get* | Allowed. Permits getting S3 resources. |
s3:DeleteStorageLensConfiguration | Allowed. Permits deleting storage lens configurations. |
s3:CreateBucket | Allowed. Permits creating S3 buckets. |
The above actions are allowed for all resources to enable S3 bucket creation, which is essential for the application to store and manage data.
AllowDynamoDB
| Permission | Description |
|---|---|
dynamodb:UpdateTimeToLive | Allowed. Permits updating time to live settings. |
dynamodb:UpdateTable | Allowed. Permits updating tables. |
dynamodb:UpdateGlobalTableSettings | Allowed. Permits updating global table settings. |
dynamodb:UpdateGlobalTable | Allowed. Permits updating global tables. |
dynamodb:UpdateContinuousBackups | Allowed. Permits updating continuous backups. |
dynamodb:UntagResource | Allowed. Permits removing tags from resources. |
dynamodb:TagResource | Allowed. Permits adding tags to resources. |
dynamodb:ListTagsOfResource | Allowed. Permits listing tags of resources. |
dynamodb:ListTables | Allowed. Permits listing tables. |
dynamodb:ListStreams | Allowed. Permits listing streams. |
dynamodb:ListImports | Allowed. Permits listing imports. |
dynamodb:ListGlobalTables | Allowed. Permits listing global tables. |
dynamodb:ListExports | Allowed. Permits listing exports. |
dynamodb:ListContributorInsights | Allowed. Permits listing contributor insights. |
dynamodb:ListBackups | Allowed. Permits listing backups. |
dynamodb:DescribeTimeToLive | Allowed. Permits describing time to live settings. |
dynamodb:DescribeTable | Allowed. Permits describing tables. |
dynamodb:DescribeContinuousBackups | Allowed. Permits describing continuous backups. |
dynamodb:DeleteTable | Allowed. Permits deleting tables. |
dynamodb:CreateTable | Allowed. Permits creating tables. |
dynamodb:CreateGlobalTable | Allowed. Permits creating global tables. |
The above actions are allowed for all resources to enable DynamoDB operations, which are essential for the application to manage and store data.
AllowSNS and AllowSQS
Our application's services use SNS and SQS for messaging communication, e.g., document ingestion pipeline, indexing pipeline, etc. Crossplane needs permissions to create and configure SQS and SNS resources for our services.
| Permission | Description |
|---|---|
sns:UntagResource | Allowed. Permits removing tags from SNS resources. |
sns:Unsubscribe | Allowed. Permits unsubscribing from SNS topics. |
sns:TagResource | Allowed. Permits adding tags to SNS resources. |
sns:Subscribe | Allowed. Permits subscribing to SNS topics. |
sns:SetTopicAttributes | Allowed. Permits setting SNS topic attributes. |
sns:SetSubscriptionAttributes | Allowed. Permits setting SNS subscription attributes. |
sns:SetEndpointAttributes | Allowed. Permits setting SNS endpoint attributes. |
sns:ListTopics | Allowed. Permits listing SNS topics. |
sns:ListTagsForResource | Allowed. Permits listing tags for SNS resources. |
sns:ListSubscriptionsByTopic | Allowed. Permits listing subscriptions by SNS topic. |
sns:ListSubscriptions | Allowed. Permits listing SNS subscriptions. |
sns:ListSMSSandboxPhoneNumbers | Allowed. Permits listing SMS sandbox phone numbers. |
sns:ListPlatformApplications | Allowed. Permits listing SNS platform applications. |
sns:ListOriginationNumbers | Allowed. Permits listing origination numbers. |
sns:ListEndpointsByPlatformApplication | Allowed. Permits listing endpoints by platform application. |
sns:GetTopicAttributes | Allowed. Permits getting SNS topic attributes. |
sns:GetSubscriptionAttributes | Allowed. Permits getting SNS subscription attributes. |
sns:GetEndpointAttributes | Allowed. Permits getting SNS endpoint attributes. |
sns:DeleteTopic | Allowed. Permits deleting SNS topics. |
sns:DeleteEndpoint | Allowed. Permits deleting SNS endpoints. |
sns:CreateTopic | Allowed. Permits creating SNS topics. |
sns:ConfirmSubscription | Allowed. Permits confirming SNS subscriptions. |
sqs:UntagQueue | Allowed. Permits removing tags from SQS queues. |
sqs:TagQueue | Allowed. Permits adding tags to SQS queues. |
sqs:SetQueueAttributes | Allowed. Permits setting SQS queue attributes. |
sqs:ReceiveMessage | Allowed. Permits receiving messages from SQS queues. |
sqs:ListQueues | Allowed. Permits listing SQS queues. |
sqs:ListQueueTags | Allowed. Permits listing tags for SQS queues. |
sqs:ListDeadLetterSourceQueues | Allowed. Permits listing dead letter source queues. |
sqs:GetQueueUrl | Allowed. Permits getting the URL of SQS queues. |
sqs:GetQueueAttributes | Allowed. Permits getting attributes of SQS queues. |
sqs:DeleteQueue | Allowed. Permits deleting SQS queues. |
sqs:CreateQueue | Allowed. Permits creating SQS queues. |
The above actions are allowed for all resources to enable SNS and SQS operations, which are essential for the application to exchange data between services.
The table below explains the permissions granted and denied in crossplane-redis.json
AllowEC2ForRedisInfrastructure
Our application's services require EC2 permissions for networking and security group management when deploying Redis clusters. Crossplane needs these permissions to configure the infrastructure for Redis deployment.
| Permission | Description |
|---|---|
ec2:DescribeSecurityGroups | Allowed. Permits describing security groups. |
ec2:DescribeSecurityGroupRules | Allowed. Permits describing security group rules. |
ec2:CreateSecurityGroup | Allowed. Permits creating security groups. |
ec2:DeleteSecurityGroup | Allowed. Permits deleting security groups. |
ec2:AuthorizeSecurityGroupIngress | Allowed. Permits authorizing security group ingress rules. |
ec2:AuthorizeSecurityGroupEgress | Allowed. Permits authorizing security group egress rules. |
ec2:RevokeSecurityGroupIngress | Allowed. Permits revoking security group ingress rules. |
ec2:RevokeSecurityGroupEgress | Allowed. Permits revoking security group egress rules. |
ec2:CreateTags | Allowed. Permits creating tags on EC2 resources. |
ec2:DeleteTags | Allowed. Permits deleting tags from EC2 resources. |
ec2:DescribeTags | Allowed. Permits describing tags on EC2 resources. |
ec2:DescribeVpcs | Allowed. Permits describing VPCs. |
ec2:DescribeSubnets | Allowed. Permits describing subnets. |
ec2:DescribeAvailabilityZones | Allowed. Permits describing availability zones. |
ec2:DescribeNetworkInterfaces | Allowed. Permits describing network interfaces. |
ec2:DescribeRouteTables | Allowed. Permits describing route tables. |
ec2:DescribeVpcEndpoints | Allowed. Permits describing VPC endpoints. |
The above actions are allowed for all resources to enable EC2 operations required for Redis infrastructure setup and management.
AllowElasticache
Our application's services use Redis for caching. Crossplane needs permissions to create and configure Redis resources for our services.
| Permission | Description |
|---|---|
elasticache:CreateUser | Allowed. Permits creating Redis users for authentication. |
elasticache:DescribeReservedCacheNodes | Allowed. Permits retrieving information about reserved cache nodes. |
elasticache:DescribeReservedCacheNodesOfferings | Allowed. Permits viewing available reserved cache node offerings. |
elasticache:DescribeEvents | Allowed. Permits retrieving ElastiCache events. |
elasticache:IncreaseReplicaCount | Allowed. Permits scaling up by adding read replicas to a cluster. |
elasticache:DescribeCacheParameterGroups | Allowed. Permits listing cache parameter groups. |
elasticache:DecreaseReplicaCount | Allowed. Permits scaling down by removing read replicas. |
elasticache:DescribeEngineDefaultParameters | Allowed. Permits viewing default engine parameters. |
elasticache:CreateGlobalReplicationGroup | Allowed. Permits creating global replication groups for cross-region replication. |
elasticache:ModifyReplicationGroup | Allowed. Permits modifying replication group settings. |
elasticache:CreateCacheCluster | Allowed. Permits creating Redis cache clusters. |
elasticache:DeleteCacheSubnetGroup | Allowed. Permits deleting cache subnet groups. |
elasticache:DescribeServiceUpdates | Allowed. Permits listing available service updates. |
elasticache:DescribeReplicationGroups | Allowed. Permits viewing details of replication groups. |
elasticache:ModifyUserGroup | Allowed. Permits modifying Redis user groups. |
elasticache:DeleteUser | Allowed. Permits deleting Redis users. |
elasticache:RemoveTagsFromResource | Allowed. Permits removing tags from ElastiCache resources. |
elasticache:DeleteUserGroup | Allowed. Permits deleting Redis user groups. |
elasticache:DeleteCacheCluster | Allowed. Permits deleting Redis cache clusters. |
elasticache:AddTagsToResource | Allowed. Permits adding tags to ElastiCache resources. |
elasticache:ModifyCacheParameterGroup | Allowed. Permits modifying cache parameter groups. |
elasticache:DescribeGlobalReplicationGroups | Allowed. Permits viewing global replication groups. |
elasticache:DescribeUsers | Allowed. Permits listing Redis users. |
elasticache:DescribeCacheClusters | Allowed. Permits retrieving details about cache clusters. |
elasticache:ListTagsForResource | Allowed. Permits listing tags associated with resources. |
elasticache:CreateReplicationGroup | Allowed. Permits creating Redis replication groups for high availability. |
elasticache:AuthorizeCacheSecurityGroupIngress | Allowed. Permits authorizing security group ingress rules. |
elasticache:DeleteCacheSecurityGroup | Allowed. Permits deleting cache security groups. |
elasticache:DescribeCacheEngineVersions | Allowed. Permits viewing available cache engine versions. |
elasticache:DescribeCacheSubnetGroups | Allowed. Permits viewing cache subnet groups. |
elasticache:CreateCacheSubnetGroup | Allowed. Permits creating subnet groups for Redis deployment. |
elasticache:DescribeSnapshots | Allowed. Permits listing Redis backups/snapshots. |
elasticache:CreateCacheParameterGroup | Allowed. Permits creating parameter groups for Redis configuration. |
elasticache:DeleteCacheParameterGroup | Allowed. Permits deleting parameter groups. |
elasticache:DescribeUserGroups | Allowed. Permits viewing Redis user groups. |
elasticache:DisassociateGlobalReplicationGroup | Allowed. Permits removing a cluster from global replication. |
elasticache:CreateCacheSecurityGroup | Allowed. Permits creating cache security groups. |
elasticache:DescribeCacheParameters | Allowed. Permits viewing cache parameters. |
elasticache:CreateUserGroup | Allowed. Permits creating Redis user groups. |
elasticache:DescribeUpdateActions | Allowed. Permits viewing available update actions. |
elasticache:ModifyUser | Allowed. Permits modifying Redis users. |
elasticache:DeleteGlobalReplicationGroup | Allowed. Permits deleting global replication groups. |
elasticache:ResetCacheParameterGroup | Allowed. Permits resetting parameter groups to defaults. |
elasticache:DeleteReplicationGroup | Allowed. Permits deleting Redis replication groups. |
elasticache:ListAllowedNodeTypeModifications | Allowed. Permits viewing allowed node type changes. |
elasticache:ModifyCacheCluster | Allowed. Permits modifying cache clusters. |
elasticache:ModifyGlobalReplicationGroup | Allowed. Permits modifying global replication settings. |
elasticache:DescribeCacheSecurityGroups | Allowed. Permits viewing cache security groups. |
elasticache:ModifyReplicationGroupShardConfiguration | Allowed. Permits modifying shard configurations. |
elasticache:ModifyCacheSubnetGroup | Allowed. Permits modifying cache subnet groups. |
The above actions are allowed for all resources to enable ElastiCache operations, which are essential for the application to manage Redis caching infrastructure.
AllowIAMForServiceLinkedRoles
Our application's services require IAM permissions for creating service-linked roles when deploying Redis clusters.
| Permission | Description |
|---|---|
iam:CreateServiceLinkedRole | Allowed. Permits creating service-linked roles for AWS services. |
The above action is allowed for all resources to enable IAM operations required for Redis infrastructure setup.
aws iam create-policy --policy-name "crossplane-provider-${CLUSTER_NAME}-boundary" --path "/web-identity/${CLUSTER_NAME}/" --policy-document file://crossplane_boundary.json && \
aws iam create-policy --policy-name "crossplane-provider-${CLUSTER_NAME}-policy" --path "/web-identity/${CLUSTER_NAME}/" --policy-document "$(< crossplane.json envsubst)" && \
aws iam create-policy --policy-name "crossplane-provider-${CLUSTER_NAME}-policy-redis" --path "/web-identity/${CLUSTER_NAME}/" --policy-document "$(< crossplane-redis.json envsubst)" && \
aws iam create-role --role-name "crossplane-provider-${CLUSTER_NAME}" --path "/web-identity/${CLUSTER_NAME}/" --assume-role-policy-document "$(< crossplane_role_trust.json envsubst)"
aws iam attach-role-policy --role-name "crossplane-provider-${CLUSTER_NAME}" --policy-arn "arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}-policy"
aws iam attach-role-policy --role-name "crossplane-provider-${CLUSTER_NAME}" --policy-arn "arn:aws:iam::${ACCOUNT_ID}:policy/web-identity/${CLUSTER_NAME}/crossplane-provider-${CLUSTER_NAME}-policy-redis"
Do not attach crossplane-provider-${CLUSTER_NAME}-boundary to any IAM role manually. It will be
attached automatically by Crossplane to the IRSA roles.
Amazon Bedrock
AlphaSense uses Amazon Bedrock to power Generative AI features.
The setup requirements are detailed in AWS documentation, with key steps highlighted below:
-
Open Amazon Bedrock in the console and select the Model access page under Bedrock configuration in the left sidebar.
-
Click Enable specific models. Select all of the required models:
- Claude Sonnet 4
- Claude 3.7 Sonnet
- Claude 3.5 Haiku
- Claude 3.5 Sonnet v2
- Claude 3.5 Sonnet
-
On the next page, enter the required company and use case details:
Field Recommended answer Who are your intended users? Internal employees Describe your use cases Grounded question-answering and search summarization Review and submit the request.
-
Repeat step 2 for each available US region:
- us-east-1
- us-east-2
- us-west-2
This is a requirement for cross-region inference, which provides improved reliability and throughput.
New AWS projects may start with lower rate limits for LLM models, especially for Anthropic Claude Sonnet, unless you proactively request a quota increase. To avoid rate limiting and ensure smooth performance, submit an AWS Support ticket to increase your daily token quota for Anthropic Claude Sonnet models.
Recommended quota increases for Sonnet 4:
- Up to 100 users: Request a tokens-per-minute quota of 2,000,000
- Up to 1,000 users: Request a tokens-per-minute quota of 4,000,000
For detailed steps on submitting a quota increase request, refer to the AWS documentation.
Kubernetes Secrets
Check the Kubernetes secrets section from the general requirements.
Telemetry
For auditing and troubleshooting purposes, you can use the built-in Grafana central hub to access the logs and metrics. Details can be found in Observability.