Additional Guidelines
1. Retrieve Your SCIM API Key
Your SCIM API key is stored inside SCIM cluster, and it is originally mapped with your company once your application deployed.
Command to get SCIM API key:
To decode the key with base64, an additional jq may need to be installed.
kubectl get secret -n platform scim-client -o json | jq -r '.data | map_values(@base64d)'
Example result:
{
"api_key": "9hFidPyTxjJC3p6X7CTEb7pQx1yc2RJQ2vm4NOBS9q99emT27okerMuvN7lsX2UE",
"company_id": "1",
"external_company_id": "your-company"
}
In the given example, your SCIM API key is: 9hFidPyTxjJC3p6X7CTEb7pQx1yc2RJQ2vm4NOBS9q99emT27okerMuvN7lsX2UE
2. Verify User is Created in AlphaSense
There are multiple ways that you can check to ensure user is created, here is the list for few of them:
- If you possess an Admin account in your deployed AlphaSense, you can locate that user through
impersonation feature:
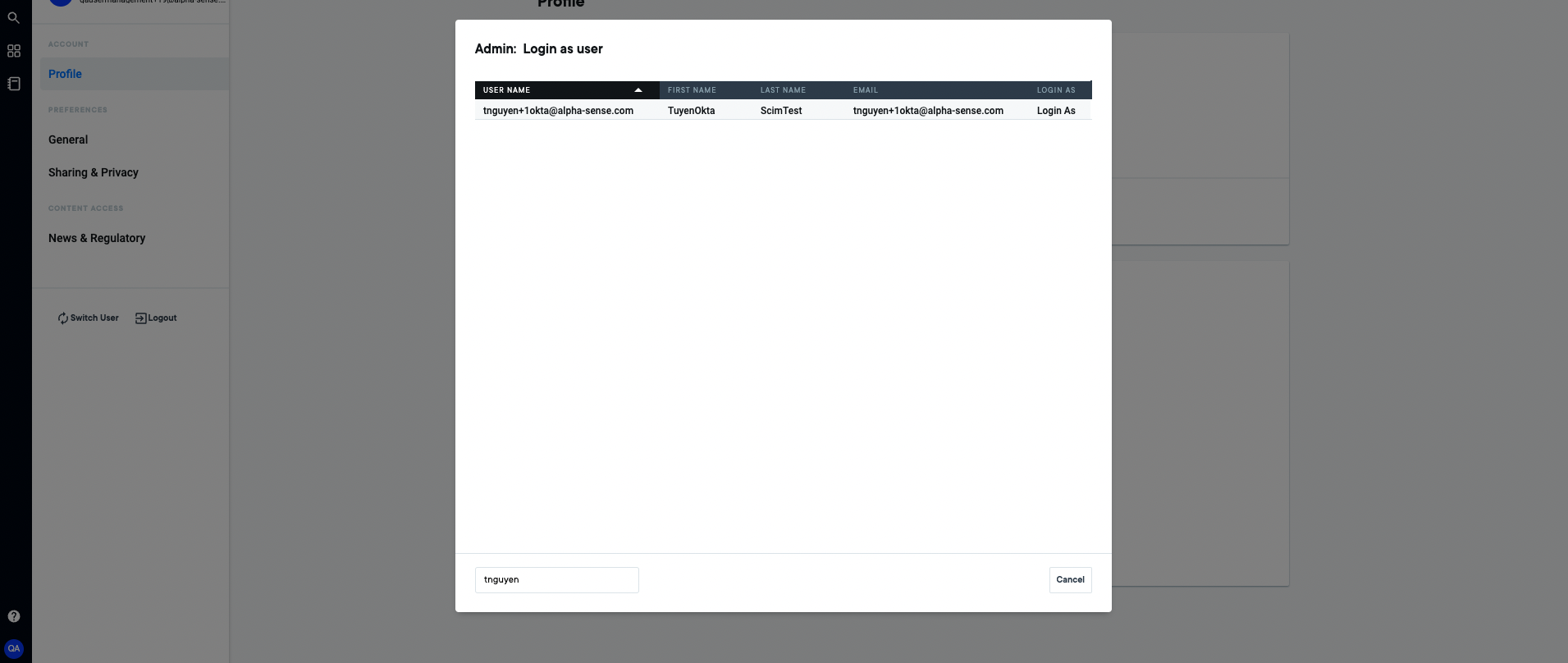
- You can search for that user under your company by email with Admin account:
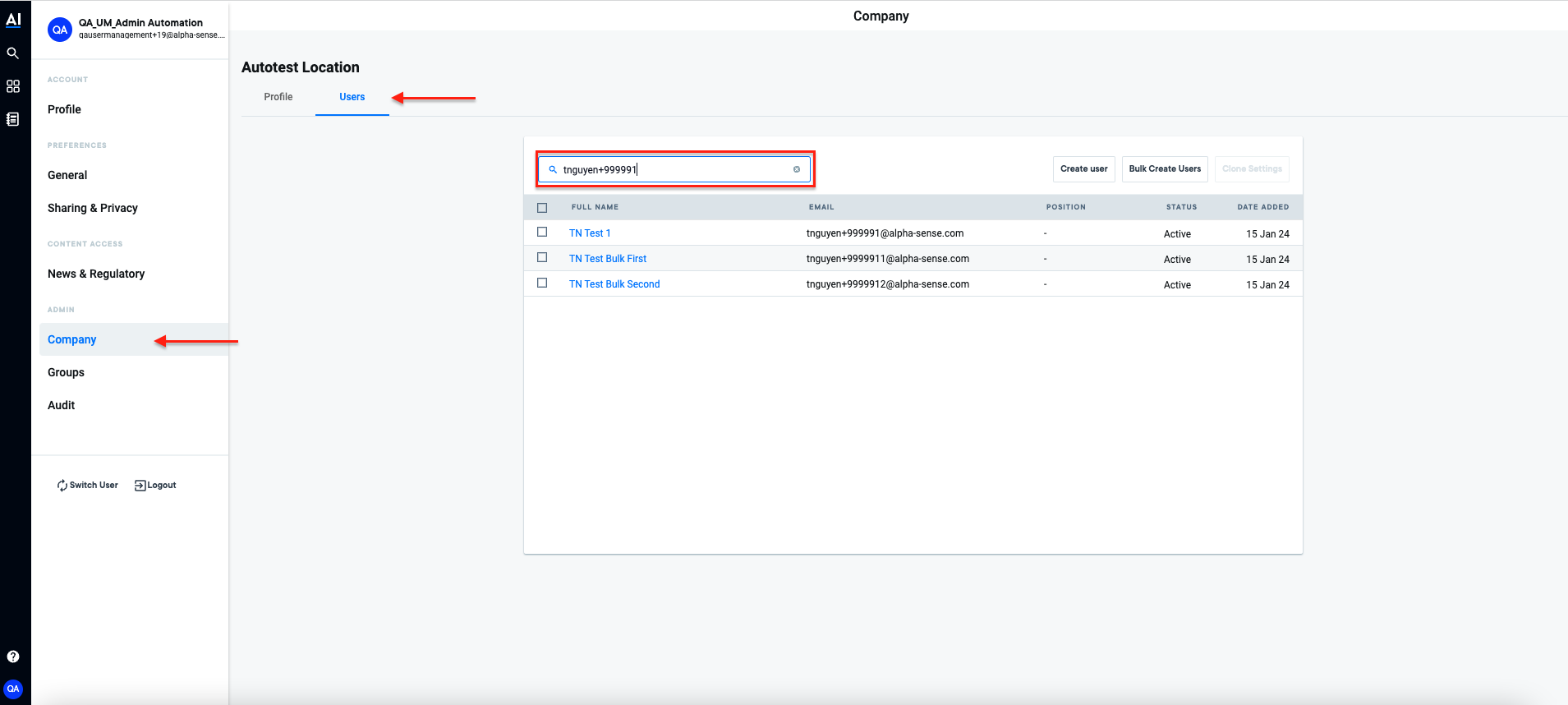
- To be added.
3. Set Up Password Upon First Time Login
This feature is currently in the development phase and accessible behind the feature flag: enterpriseLogin.
Format: {domain name}/?features=enterpriseLogin
- Log into your deployed AlphaSense application with newly created/onboard user:
- Option 1: User onboard through SCIM - The below example user was created in AzureAD and
synced through SCIM API to your AlphaSense system, and the user id here is user principal
username (which is already defined in AzureAD for that specific user):
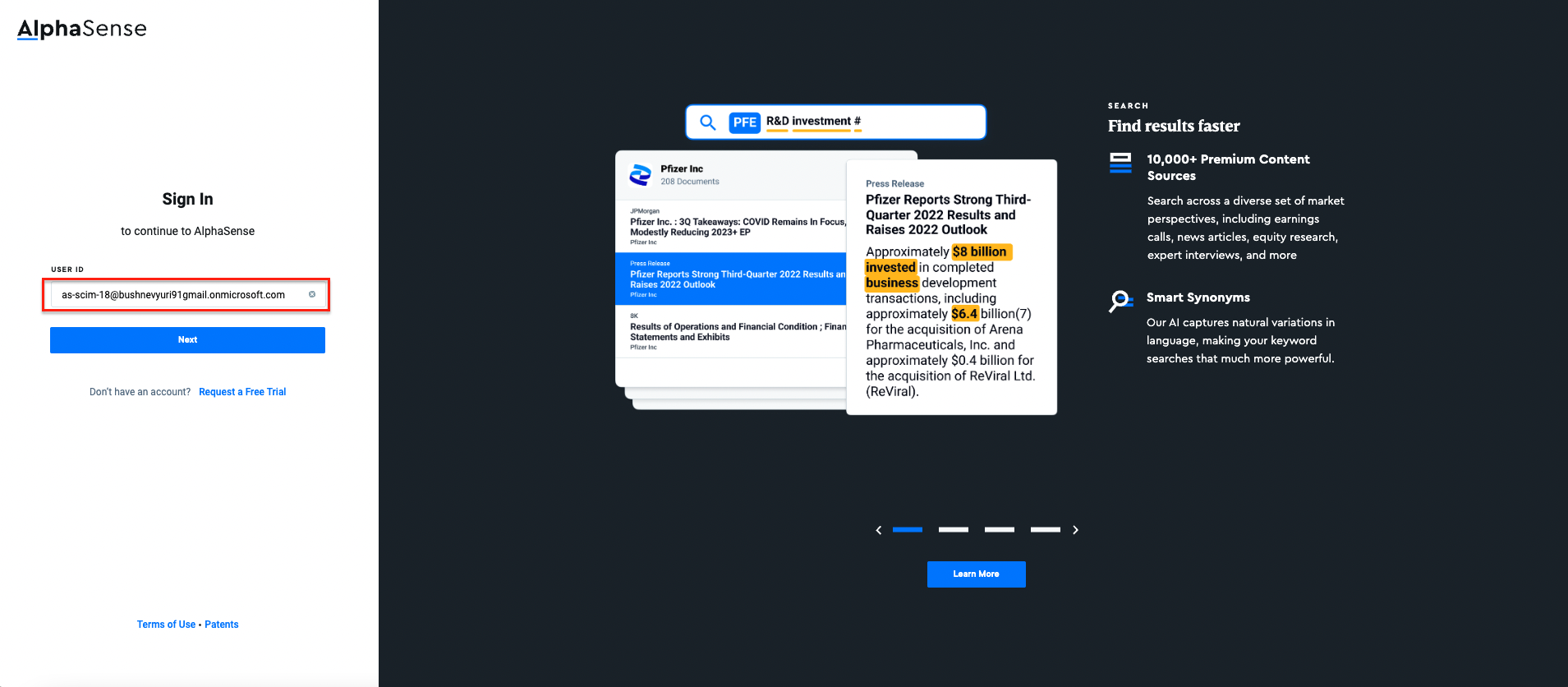
- Option 2: User created with Admin View feature - The below example user is created by
AdminView and the user id here is its email:
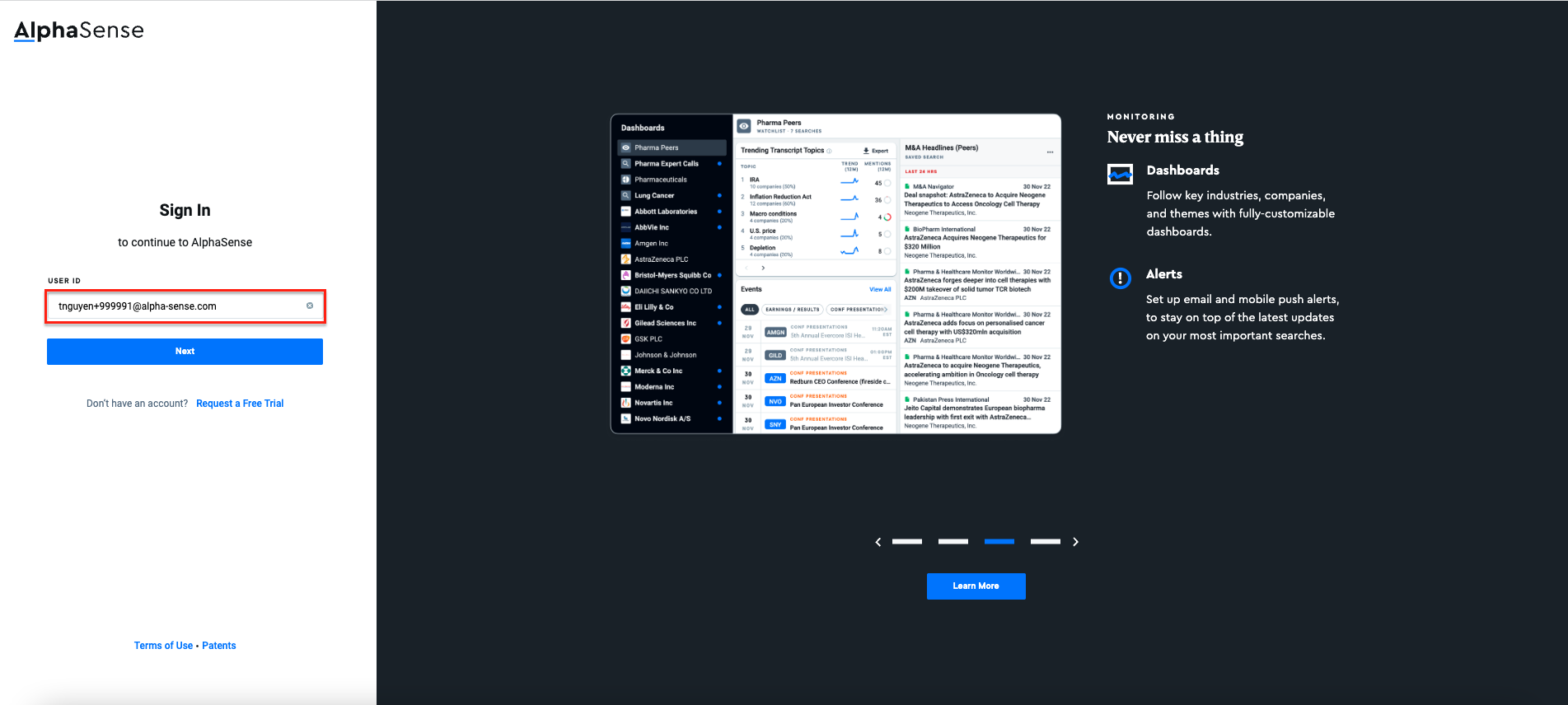
- Option 1: User onboard through SCIM - The below example user was created in AzureAD and
synced through SCIM API to your AlphaSense system, and the user id here is user principal
username (which is already defined in AzureAD for that specific user):
- Click Request Setup Instruction for first time password setup:
- New email will be sent to user mailbox for setting new password:
- Example for user onboard through AzureAD:
- Example for user created in Admin View:
- Example for user onboard through AzureAD:
- Login to account’s assigned mailbox:
- Option 1: With users onboard through SCIM - The service provider will maintain this email
value. Below example is AzureAD - Microsoft Entra ID, the associated mailbox should be
Outlook - Email and password are previously defined while onboarding user in AzureAD:
- Option 2: With users created in AdminView - Login to dedicated mailbox associated with email
of specific user, the email of user was pre-defined in user creation process:
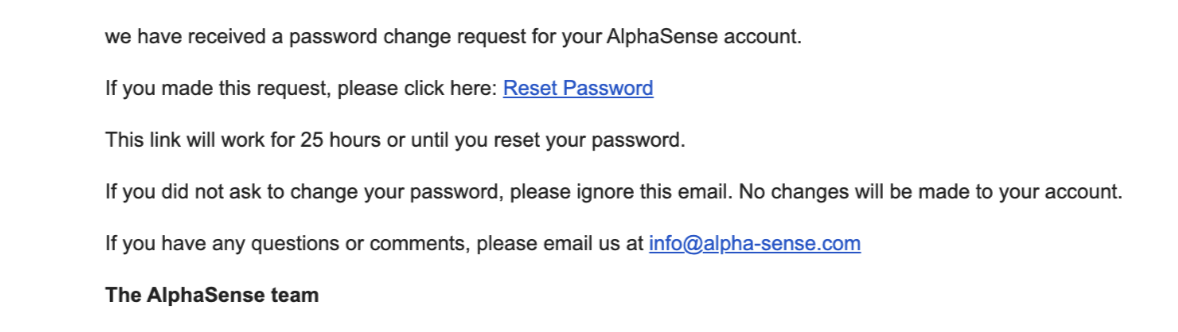
- Option 1: With users onboard through SCIM - The service provider will maintain this email
value. Below example is AzureAD - Microsoft Entra ID, the associated mailbox should be
Outlook - Email and password are previously defined while onboarding user in AzureAD:
- Click on generated link inside the email to navigate to setting password page.
- Enter your desired password and confirm it again:
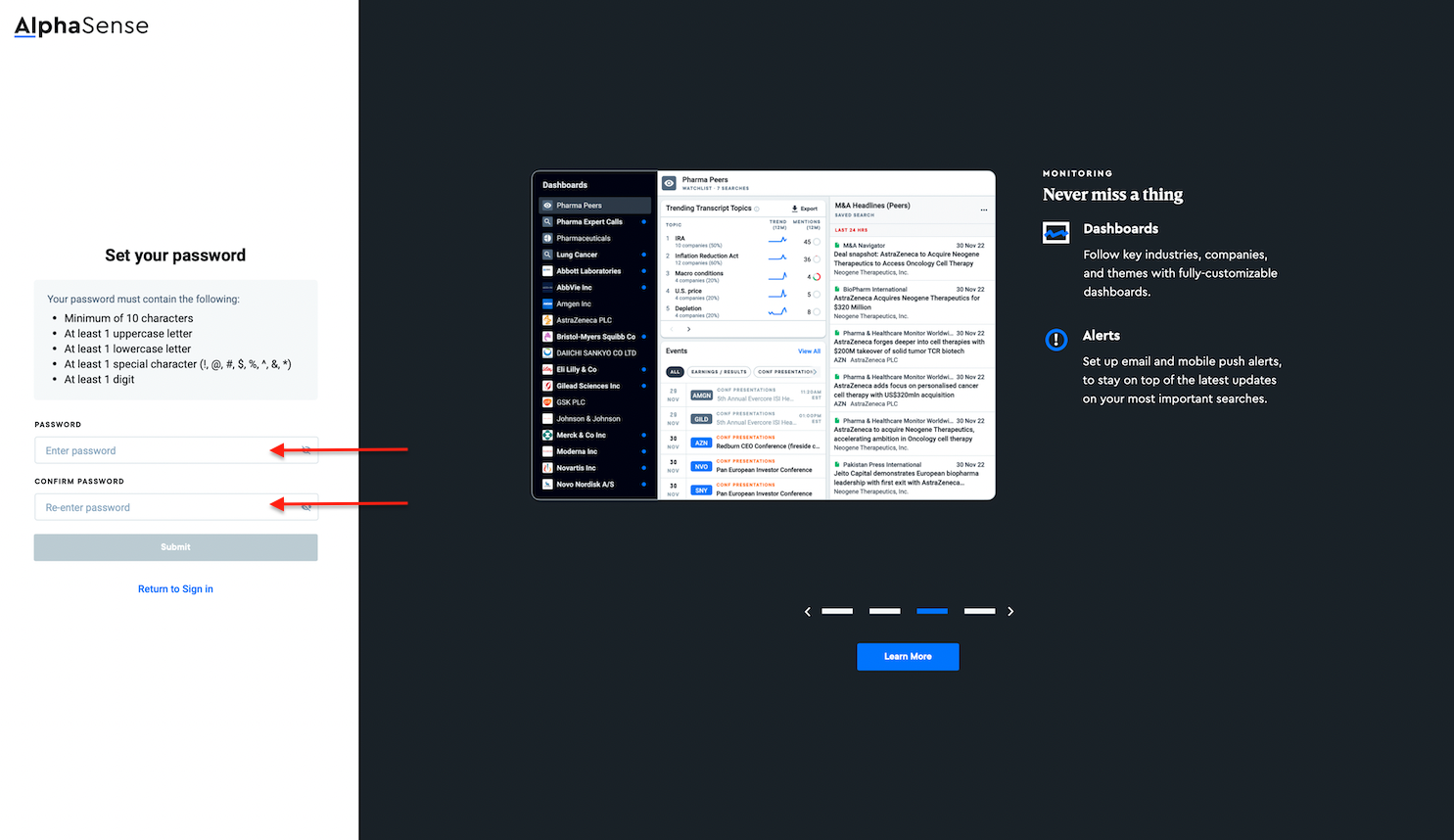
- Now you can successfully log into your deployed AlphaSense with new password.
4. Extract configuration values from AlphaSense SSO system metadata
The AlphaSense team will provide the metadata file for customers using AlphaSense SaaS product. For those on Enterprise Private Cloud product, the SAML metadata file can be accessed at {domain name}/services/sso-ws/saml/metadata.
Sample metadata XML file:
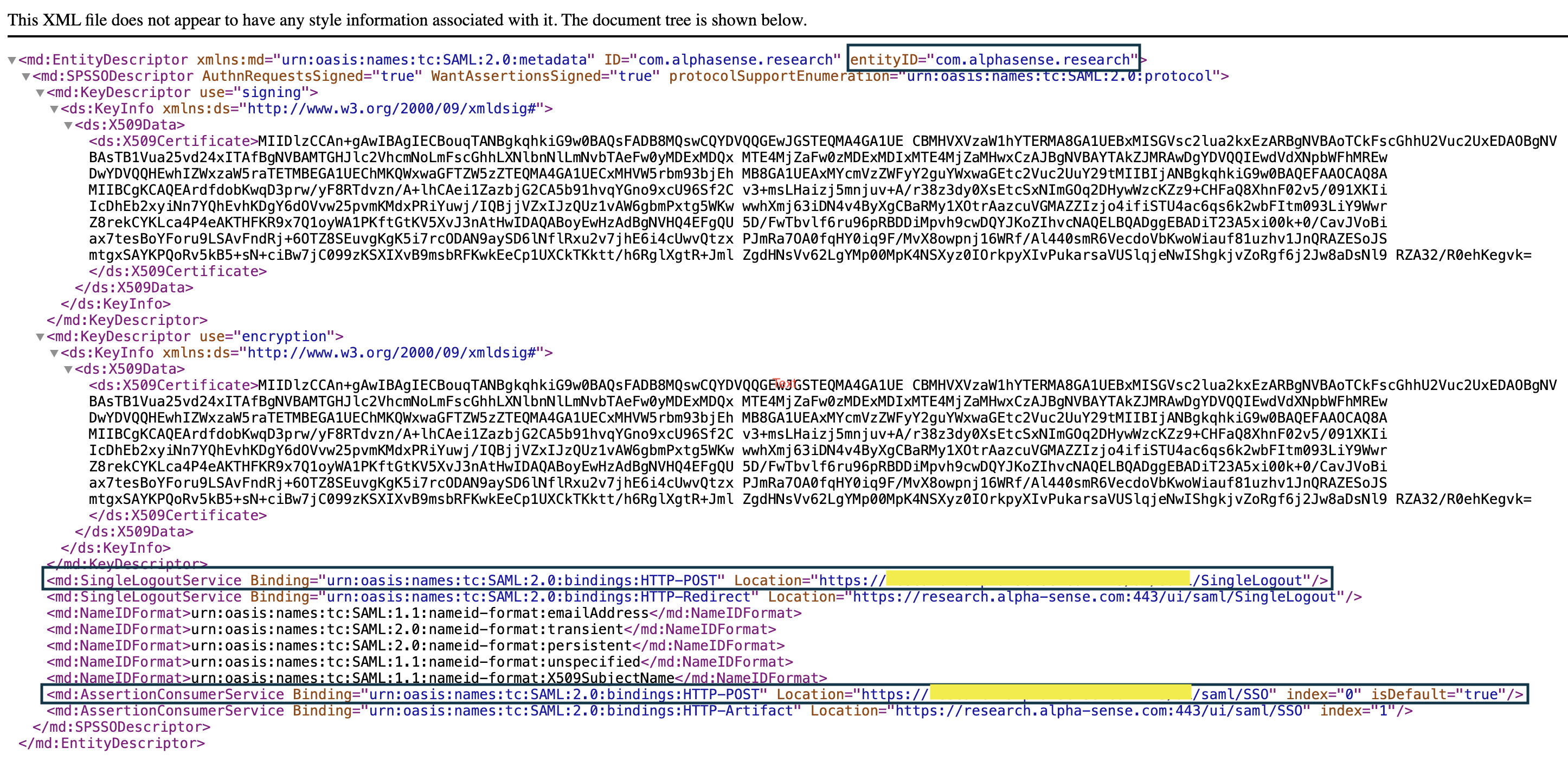 All below configuration values are only for instruction purpose, the real values may vary.
All below configuration values are only for instruction purpose, the real values may vary.
4.1 EntityID
The entityID or saml-entityid is specified in <EntityDescriptor> tag. For example:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="com.alphasense.research" entityID="com.alphasense.research">
In this case, the extracted entityID is com.alphasense.research.
4.2 SingleLogoutURL
This is optional and specified in <SingleLogoutService> tag. For example:
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://your-domain/services/sso-ws/saml/SSO/SingleLogout"/>
The value we can extract here for single logout URL is https://your-domain/services/sso-ws/saml/SSO/SingleLogout.
4.3 AssertionConsumerServiceURL
This is known as Single sign-on URL in Okta or Reply URL in Microsoft Entra ID and can be extracted from <AssertionConsumerService> tag. For example:
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://your-domain/services/sso-ws/saml/SSO" index="0" isDefault="true"/>
From this, the assertion consumer service URL is https://your-domain/services/sso-ws/saml/SSO.